Next: TokenDelay Up: The readout Previous: Daisy chain mode
![]()
![]()
![]()
![]()
Next: TokenDelay
Up: The readout
Previous: Daisy chain mode
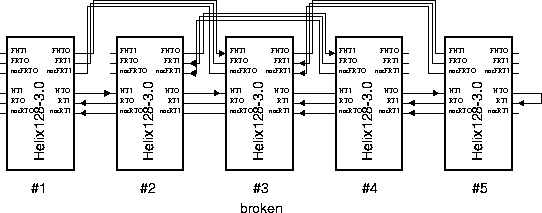 |
Every chip is not only connected to its predecessor and successor in
the daisy chain, but also to the second predecessor and successor
(fig. 15). When a chip has sent its data
it sends a token via the HelixTokenOut and
FailsafeHelixTokenOut ports ![]() .
.
These tokens are routed to the chip's successor's HelixTokenIn port and to the second successor's FailsafeHelixTokenIn port. Normally, a chip starts transmission of data when the token arrives at the HelixTokenIn port. The successor of a broken chip can be programmed to start transmission of data upon reception of a token on its FailsafeTokenIn port.
The same mechanism is implemented for the ReturnToken ports.
The failsafe token mechanism is programmable via the bit 4 ...7 of the clock divider register.
Table 4.6.2 shows all bits necessary for controlling the mechanism.
| Bitname | Explanation | Number |
| BypassHelixToken | If 0 then HelixTokenIn is activated, if 1 then FailsafeHelixTokenIn is activated | 4 |
|---|---|---|
| BypassReturnToken | If 0 then ReturnTokenIn is activated, if 1 then FailsafereturnTokenIn is activated | 5 |
| LastInChain | If this chip is the last in the chain, this bit must be set to 1 | 6 |
| FirstInChain | If this chip is the first in the chain, this bit must be set to 1 | 7 |
[Definition of failsafe token control bits] Definition of failsafe token control bits and bit number in the ClkDiv register
Martin Feuerstack